15. Exercise: Frameworks in Practice
Below is an excerpt from a basic completed risk framework. Review the excerpt and keep it in mind when answering the questions below.
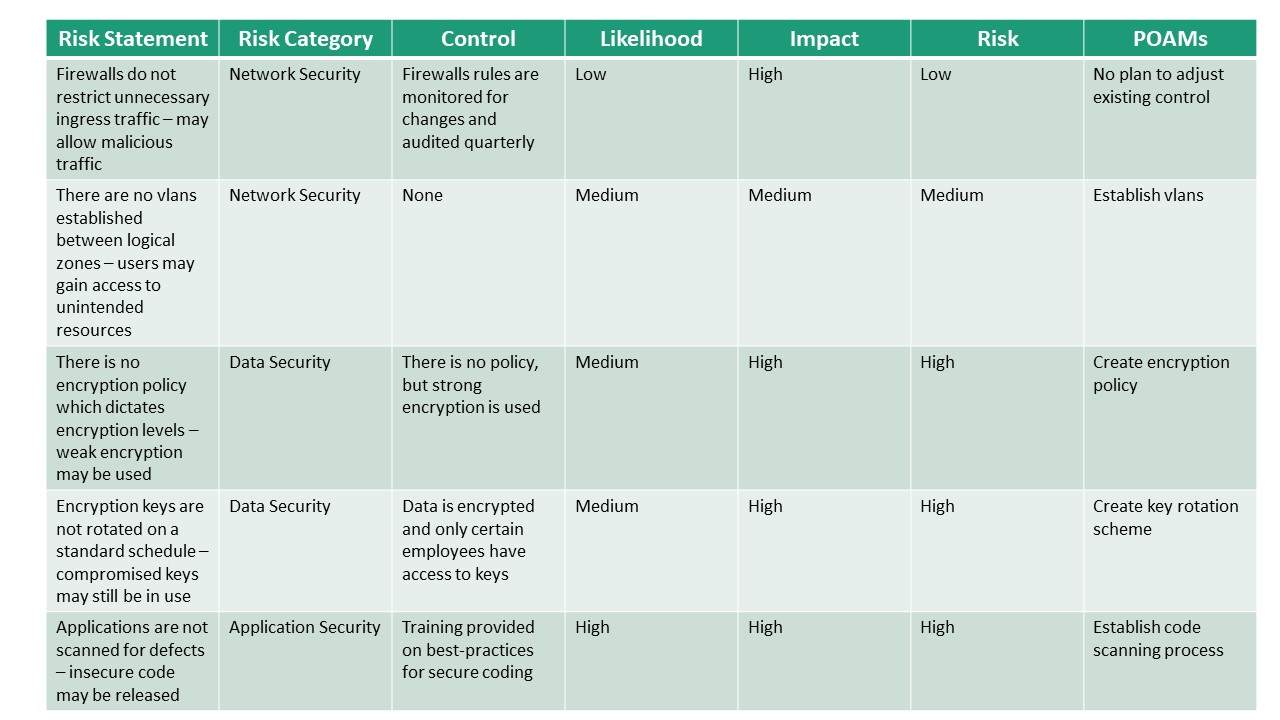
Risk Management Framework Matching
QUIZ QUESTION::
Match the statements below to the appropriate part of a risk management framework.
ANSWER CHOICES:
|
Statement |
Parts of the framework |
|---|---|
A statement that segregation of duties does not exist within the database management function and could cause data leakage |
|
An assessment that exploitation of an operating system vulnerability would result in "minimal" damage. |
|
A statement that temporary passwords are all initially set to the same password which could result in account hijacking. |
|
An assessment that the residual risk of allowing unsigned SMB traffic is "medium" given an assessment of the likelihood and impact of the vulnerability. |
|
"Database Security" used as a convention for grouping several risk statements. |
|
A plan to implement continuous firewall monitoring to address a number of risks associated with an organization's firewalls. |
|
A firewall which disallows all ingress traffic other that port 443 |
SOLUTION:
|
Statement |
Parts of the framework |
|---|---|
|
A plan to implement continuous firewall monitoring to address a number of risks associated with an organization's firewalls. |
|
|
An assessment that the residual risk of allowing unsigned SMB traffic is "medium" given an assessment of the likelihood and impact of the vulnerability. |
|
|
"Database Security" used as a convention for grouping several risk statements. |
|
|
A statement that segregation of duties does not exist within the database management function and could cause data leakage |
|
|
A statement that temporary passwords are all initially set to the same password which could result in account hijacking. |
|
|
A statement that segregation of duties does not exist within the database management function and could cause data leakage |
|
|
A statement that temporary passwords are all initially set to the same password which could result in account hijacking. |
|
|
A firewall which disallows all ingress traffic other that port 443 |
|
|
An assessment that exploitation of an operating system vulnerability would result in "minimal" damage. |
Risk Management Framework Matching
QUIZ QUESTION::
Match the statements below to the appropriate part of a risk management framework.
ANSWER CHOICES:
|
Statement |
Parts of the Framework |
|---|---|
"Encryption Management" used as a convention for grouping several risk statements. |
|
An assessment that it is unlikely that an attacker could social engineer their way into an organization's data center. |
|
A procedure which details appropriate steps for users to change their system passwords. |
|
A statement that database tables contain information about different customers in the same table which might result in data leakage. |
|
A plan to address multi-factor authentication deficiencies by Jun 18th. |
SOLUTION:
|
Statement |
Parts of the Framework |
|---|---|
|
A procedure which details appropriate steps for users to change their system passwords. |
|
|
A plan to address multi-factor authentication deficiencies by Jun 18th. |
|
|
An assessment that it is unlikely that an attacker could social engineer their way into an organization's data center. |
|
|
"Encryption Management" used as a convention for grouping several risk statements. |
|
|
A statement that database tables contain information about different customers in the same table which might result in data leakage. |